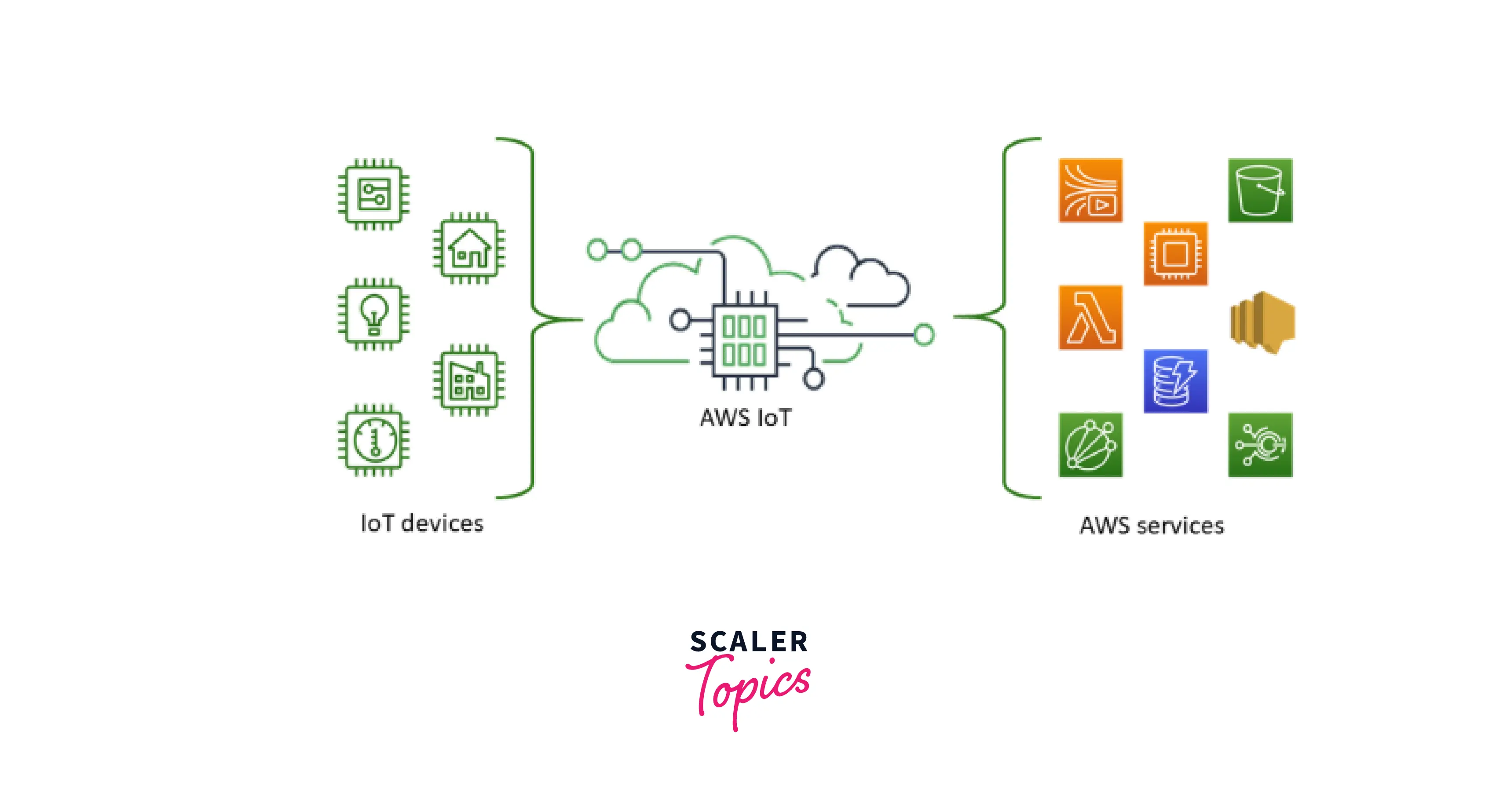
When we talk about keeping our connected devices safe, the idea of secure access comes up pretty quickly. You see, the Internet of Things, or IoT as it's often called, describes a vast collection of physical items – like appliances in your home or perhaps sensors out in a field – that have little brains, some software, and ways to chat with other gadgets and systems over the internet. These "things" are always gathering and sharing data, and that, is that, means we need really good ways to make sure only the right people or systems can get to them. It's about protecting all that information as it moves around.
A big part of making sure these smart devices stay private and safe involves something called Secure Shell, or SSH. This is a well-known way to create a private, encrypted connection between devices, even when they're talking over a network that might not be so private itself. For many years, SSH has been a go-to tool for folks who manage computer systems, offering a way to log in and control things from afar without worrying too much about prying eyes. But, you know, when you think about the unique needs of IoT, a standard SSH setup might not always fit just right, so, there's a bit more to consider.
This is where a specialized version, sometimes referred to as IoT Core SSH, steps in. It's a bit like the regular SSH you might know, but it's been changed and shaped to handle the particular demands of those many, many connected devices. It keeps the core idea of secure communication, but it adds features and ways of working that are much better suited for the kind of environment where IoT devices live. We're going to look closely at what makes these two similar and how they differ, especially when thinking about keeping your IoT world secure and running smoothly, very much so.
Table of Contents
- What is the Internet of Things (IoT)?
- How Does Secure Shell (SSH) Work?
- Why is IoT Core SSH Different from Regular SSH?
- What Makes AWS IoT Core SSH a Strong Option?
- Can You Really Connect Directly to IoT Devices with SSH?
- How Does IoT Core SSH Tunneling Help with Security?
- What Are the Benefits of Integrating SSH with AWS IoT Core?
- Looking Ahead - The Future of IoT Core SSH vs SSH
What is the Internet of Things (IoT)?
The Internet of Things, or IoT, describes a really big collection of physical items. These are things that have little brains inside, like sensors and some software, and other bits of technology that let them talk to each other and to bigger systems over the internet. You see, these objects can collect information, process it a little, and then send it on, all without a person needing to tell them what to do. It’s a network where physical things are connected and can swap data, which is pretty neat.
When someone talks about IoT, they're referring to this whole network of gadgets, vehicles, home appliances, and just about any other physical object you can think of. These items are fitted with those sensors, that software, and the network connections that make them smart. They're designed to communicate and exchange information, creating a kind of digital awareness of the physical world. The idea was first brought up by a computer scientist, and it has grown a lot since then, almost becoming a part of our daily routine, in a way.
So, IoT stands for the Internet of Things, and it really points to how all these physical devices, like your fridge or your car, are hooked up to each other. They have their own software, their own sensors, and ways to connect. This setup allows them to transfer data back and forth without people getting involved directly, making the physical world a bit more digitally aware. It's about how technology helps these items interact with very little human help, gathering and sharing information, which is quite fascinating, really.
The term IoT, in essence, covers the entire network of these connected devices and all the technology that helps them talk to the cloud, and also to each other. It’s about creating a world where everyday objects can collect details and share them, making things smarter and sometimes, a bit more helpful. These devices are typically made with built-in sensors and other bits that allow them to connect and share data with other IoT items and with cloud services, which is pretty much how they operate.
How Does Secure Shell (SSH) Work?
Secure Shell, or SSH, is a method used to make sure that when devices talk to each other over a network that isn't totally safe, their conversation stays private and encrypted. It’s like having a secret code that only your devices know, so anyone else trying to listen in just hears gibberish. In the context of the Internet of Things, SSH plays a really important part. It gives us a secure way to communicate, letting us manage and work with those many connected gadgets from far away, you know, without worrying about someone else snooping.
This tool is quite helpful for keeping sensitive information safe as it travels between devices. It does this by taking the data and scrambling it up into encrypted packets, and it also checks to make sure that the people or systems trying to connect are who they say they are. This way, SSH makes sure that the information remains private and that only authorized users can get to it. It’s a very good way to protect your digital conversations, especially when those conversations are happening across a network that isn't entirely private, which is often the case, so.
One of the ways it helps with security in IoT networks is by providing a channel for communication that is protected. It means that when your smart thermostat talks to your phone, or when you need to send a command to a sensor in a far-off location, that connection is safe. SSH is a crucial piece of the puzzle for keeping those IoT networks protected, allowing devices to communicate without exposing their information to others. It’s a foundational piece of security for many systems, truly.
Basically, SSH provides a secure way for two devices to talk, even if they are on an open network. It makes sure that the information exchanged is kept secret and that both sides of the conversation are who they claim to be. This is especially important for IoT devices, where there are often many points of connection and a lot of valuable information being moved around. It's a bit like having a private telephone line in a very public place, very much so.
Why is IoT Core SSH Different from Regular SSH?
IoT Core SSH is a special kind of the usual SSH protocol. It's been changed and made to fit the particular needs of environments where you have lots of connected devices. While it keeps the basic idea of SSH, it's set up to work better with how IoT systems are built and managed. You see, traditional SSH often expects a direct, open connection to a device, but with IoT devices, that's not always how things work, so there are some differences.
For example, you typically can't just start a direct SSH session into an IoT device. This is often because the device's own security, like a firewall, will block all incoming connections. This is a good thing for security, but it means you need a different approach to get in and manage the device. IoT Core SSH helps with this by working with cloud services to create a pathway around these blocks, making it possible to reach devices that are otherwise tucked away behind their own defenses, which is pretty clever, you know.
The standard way of doing things might show you how to open a tunnel, and then you use that tunnel to start your SSH session. IoT Core SSH, particularly when used with services like AWS, takes this idea and makes it much more suited for the scale and security demands of many, many devices. It's not just about getting in, but getting in safely and efficiently, which is a big deal when you have thousands of devices to look after. It's almost like having a specialized key for a very specific type of lock, you could say.
So, the core difference lies in how it handles connections to devices that are often behind strict firewalls or don't have public-facing IP addresses. IoT Core SSH lets you set up your devices to respond to a command from the IoT Core service and then open a reverse SSH connection to a specific address. Of course, you need to be able to get to the device in the first place to set this up, so you have to think about that initial access point. This method provides a flexible way to manage devices that are otherwise hard to reach directly, which is quite helpful, actually.
What Makes AWS IoT Core SSH a Strong Option?
AWS IoT Core SSH is a very helpful tool that allows for secure remote access to IoT devices. It uses the Secure Shell protocol, but it does so within the Amazon Web Services environment. This means it brings together the security of SSH with the large-scale management features of AWS IoT Core. It's a way to make sure that when you need to get into your devices from far away, that connection is protected and reliable, which is a big concern for many people, you know.
The way it works is by combining the secure communication abilities of SSH with the powerful management and connection features that AWS IoT Core offers. This combination creates a strong defense, bringing together the benefits of AWS cloud services with the proven security that SSH tunneling provides. It’s like having a very secure pipeline for your device communications, which is pretty much what you want when dealing with important data. This integration makes it a formidable choice for keeping your IoT operations safe and running smoothly, which is often a primary goal.
Amazon Web Services provides good tools for looking after IoT devices, and one of the most important parts of this whole process is making sure SSH works well with IoT Core. AWS IoT Core itself gives you a platform that can grow with your needs and is secure for managing all your devices. Then, SSH adds those encrypted communication channels. So, when you put them together, you get a system that is both flexible and very secure, which is quite important for modern setups, truly.
Integrating SSH within the AWS setup not only makes things more secure but also uses AWS's very strong infrastructure to make sure that your IoT operations run without a hitch. It simplifies the whole process by putting SSH protocols right into AWS IoT Core, giving you a very easy way to manage and fix problems on your devices from anywhere. This approach helps businesses make their security better and also makes device management much simpler, which can save a lot of time and effort, you know.
Can You Really Connect Directly to IoT Devices with SSH?
When it comes to connecting to IoT devices, the idea of a direct SSH session might seem like the simplest way. However, as we touched on earlier, you often can't just start a direct SSH session into an IoT device. This is usually because the device's firewall is set up to block all incoming traffic, which is a good security measure to keep unwanted visitors out. This means that while SSH is the tool, the method of connecting needs to be a bit different from how you might connect to a regular server, which is an important distinction, you know.
The standard tutorials for SSH often show you how to open a tunnel first, and then you use that tunnel to begin your SSH session. This concept is still very much at play with IoT devices, but it's often managed by the IoT Core service itself. Instead of you manually setting up a tunnel every time, the IoT Core service can help orchestrate this secure pathway. It’s a way to get around those inbound traffic blocks while still using the secure nature of SSH, which is pretty clever, you know.
What you can do, for example, is set up your devices to react to a specific command from IoT Core. When they get this command, they can then open a reverse SSH connection back to a specific IP address that you control. This means the device itself initiates the connection, rather than waiting for an incoming one, which bypasses the firewall's typical blocking behavior. Of course, you need to have access to the device initially to add this capability, so that’s something to think about right from the start. This method offers a secure and practical way to reach devices that are otherwise hard to access, which is often the case with IoT deployments, naturally.
So, while you might not establish a "direct" connection in the traditional sense of initiating it from your side, you can absolutely use SSH to communicate with these devices. The key is understanding that the connection might be "reversed" or "tunneled" through a service like AWS IoT Core. This approach ensures that even with strict firewall rules, you can still securely manage and troubleshoot your devices, which is a very practical solution, really.
How Does IoT Core SSH Tunneling Help with Security?
IoT SSH tunneling, especially when used with AWS, provides a very strong defense for your connected devices. It brings together the power of AWS cloud services with the proven security of SSH tunneling. This combination creates a secure and private pathway for your device communications, making it much harder for unauthorized people to listen in or interfere. It's a bit like building a private, protected road for your data to travel on, which is quite important, you know, for sensitive information.
In the world of IoT, SSH serves as a very important tool for protecting sensitive information that gets sent between devices. By taking data packets and scrambling them up through encryption, and also by checking to make sure that users are who they claim to be, SSH makes sure that the information stays private and safe. This tunneling method extends that protection, creating a secure communication channel even when the devices are on a network that might not be secure itself. It’s a fundamental layer of defense for your IoT network, truly.
One such security method that plays a really important part in keeping IoT networks safe is Secure Shell, commonly known as SSH. SSH provides a secure way for devices to talk, enabling encrypted communication. When you add tunneling to this, especially through a cloud service, you're essentially creating a hidden, protected route for your data. This helps protect against various threats, like someone trying to intercept your data or trying to get unauthorized access to your devices. It’s a key piece of making sure your IoT setup is as secure as possible, very much so.
This approach means that even if a device is behind a firewall or on a public network, the data it sends and receives through the SSH tunnel is protected. It prevents direct exposure of the device to the internet, reducing its vulnerability to attacks. The tunnel acts as a shield, ensuring that all communications are private and authenticated. This robust defense mechanism is crucial for maintaining the integrity and confidentiality of your IoT ecosystem, which is something you really want to have in place, you know.
What Are the Benefits of Integrating SSH with AWS IoT Core?
Integrating Secure Shell (SSH) with AWS IoT services offers several good things for businesses. First off, it can really make your security stronger. By using SSH, you're adding a layer of encrypted communication, which means that the information flowing between your devices and your management systems is kept private and safe from prying eyes. This is a big deal when you're dealing with sensitive data or controlling important equipment, so it helps you sleep a bit better at night, you could say.
Beyond just security, this combination also helps to make device management much simpler and more efficient. AWS IoT Core provides a scalable and secure platform for looking after your devices. When you add SSH to this, it means you have a straightforward way to remotely manage and fix problems with those devices. You don't have to be physically next to each device to update software, check status, or troubleshoot issues, which is a huge time-saver, especially when you have many devices spread out over a large area, very much so.
Understanding how to use AWS IoT Core SSH effectively can really improve your ability to control and secure your connected devices. It helps ensure that your operations run smoothly and efficiently. This integration leverages AWS's strong infrastructure, meaning you get the benefit of a highly reliable and available system. It's about making sure your IoT setup is not only safe but also easy to handle, which is a practical concern for many businesses, naturally.
Essentially, AWS IoT Core SSH is a service that lets you connect to and manage your IoT devices securely using those SSH protocols. AWS IoT Core acts as the main support for this, providing the framework that handles all the connections and data. This makes it a very powerful combination for anyone who needs to keep their IoT devices secure and well-managed, without having to build everything from scratch. It's almost like having a ready-made secure access system for your entire fleet of connected things, you know.
Looking Ahead - The Future of IoT Core SSH vs SSH
The future of IoT SSH on AWS looks quite promising, thanks to the continuous advancements in both cloud services and security protocols. As more and more devices become connected and the Internet of Things grows, the need for robust and flexible remote access solutions will only increase. We can expect to see even more refined ways for IoT Core SSH to interact with devices, making it even simpler and more secure to manage them from afar. It's a field that is always getting better, which is a good thing for everyone involved, truly.
The ongoing development in this area means that the differences between a traditional SSH approach and an IoT Core SSH approach will likely become even more pronounced. IoT Core SSH will continue to be tailored to the specific challenges of managing devices that might be resource-limited, located in hard-to-reach places, or operating behind strict network boundaries. This specialization is what makes it so valuable for large-scale IoT deployments, as it addresses issues that a standard SSH setup might not handle as gracefully, you know.
As the Internet of Things expands into more aspects of our lives, the importance of secure and efficient device management becomes even more critical. Solutions like AWS IoT Core SSH will continue to be vital in providing that secure backbone for communication and control. They help ensure that the vast array of physical objects, equipped with their sensors and software, can interact safely and reliably without constant human intervention. It’s a key piece in making the connected world work well, which is something we all benefit from, actually.
So, when you consider the ongoing push for more connected devices and the increasing amount of data they handle, the role of specialized security tools like IoT Core SSH becomes very clear. It’s about making sure that these systems are not just connected, but connected safely and managed effectively. This ongoing evolution of secure access methods is what will help drive the broader adoption and continued success of IoT across many different industries and applications, which is quite exciting to think about, you know.